On why MalwareTech was the first to find the WannaCry killswitch
A lof of people have been talking about how it is suspicious that MalwareTech was the first person to find the WannaCry killswitch. I thought that the only people thinking this would be those without experience in reverse engineering or malware research, so I was very surprised and disappointed to see what Dave Aitel of Immunity, Inc tweeted about the matter:
https://t.co/qKBo8jLR27 This is probably not good news...
— daveaitel (@daveaitel) August 5, 2017
First let’s discuss what MalwareTech actually did for work. He was employed by a cybersecurity firm, Kryptos Logic, to track the spread of botnets. The way they did this was to usually try to “sinkhole” the botnet’s command and control (C2) servers. There are many ways in which one could do this but they usually involve either registering DGA (Domain Generation Algorithm) domains before the botnet controller could and pointing those domains at his companies sinkhole server, or find a domain the bot connects to which isn’t registered yet and register it before the botnet controller does. Once the bots were connecting to the sinkhole server it would track all IP addresses belonging to the botnet, so that affected companies can be notified, and generate reports on the spread of the botnet and how many affected hosts there are.
Now lets take a look at the WannaCry ransomware. The sample I am using has the hash b9318a66fa7f50f2f3ecaca02a96268ad2c63db7554ea3acbde43bf517328d06 for those of you wanting to follow along at home.
First, lets take a look at the hybrid-analysis report on this sample: https://www.hybrid-analysis.com/sample/b9318a66fa7f50f2f3ecaca02a96268ad2c63db7554ea3acbde43bf517328d06?environmentId=100. This is a generic report similar to one generated by any other dynamic analysis tool (Cuckoo sandbox etc). One of the first things an analyst will look at is the strings the binary contains, this can give a quick idea of the kind of things the malware is doing or hint at whether the malware is packed or not. A quick scroll through the strings or a quick search for “.com” and look at what we find:
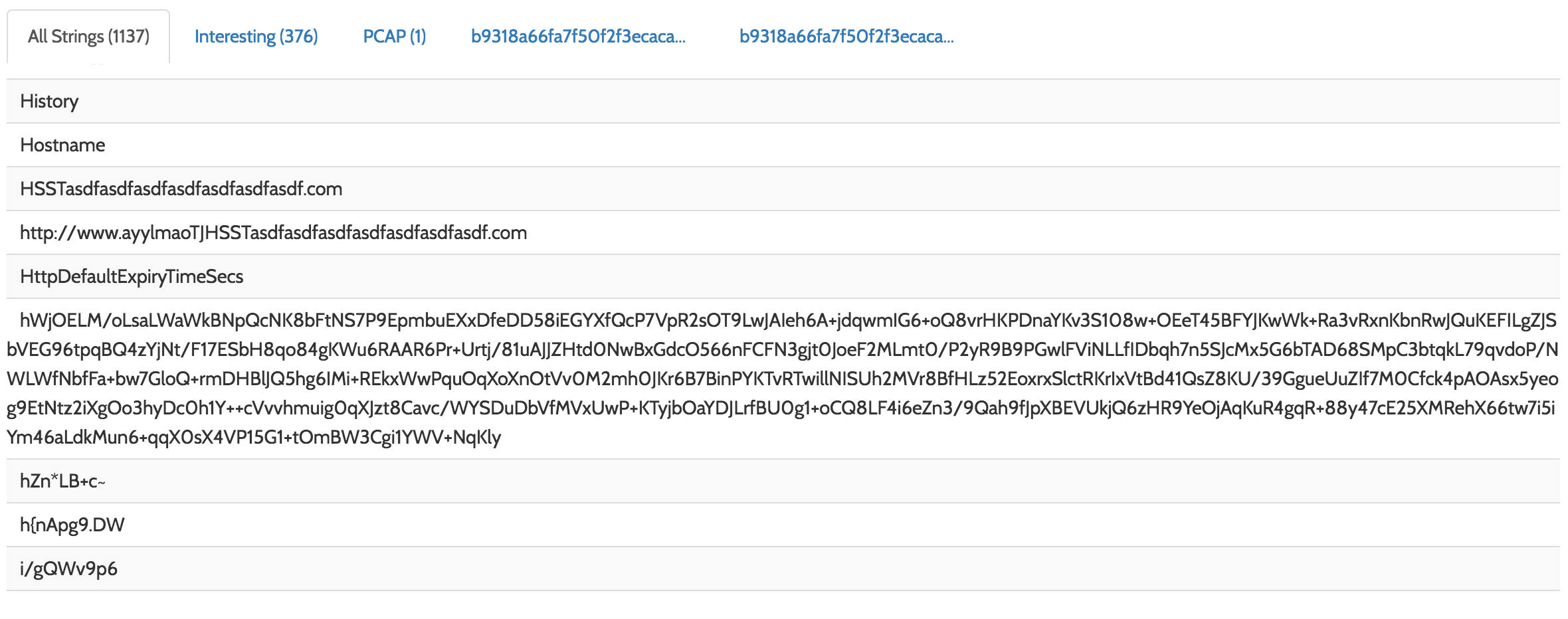
Oh wow, look at that, it’s the killswitch domain!
Let’s take a different approach and read the rest of the report.. usually an analyst will take a look at the network traffic (either using wireshark or the report after a quick sandbox run, such as we are doing).
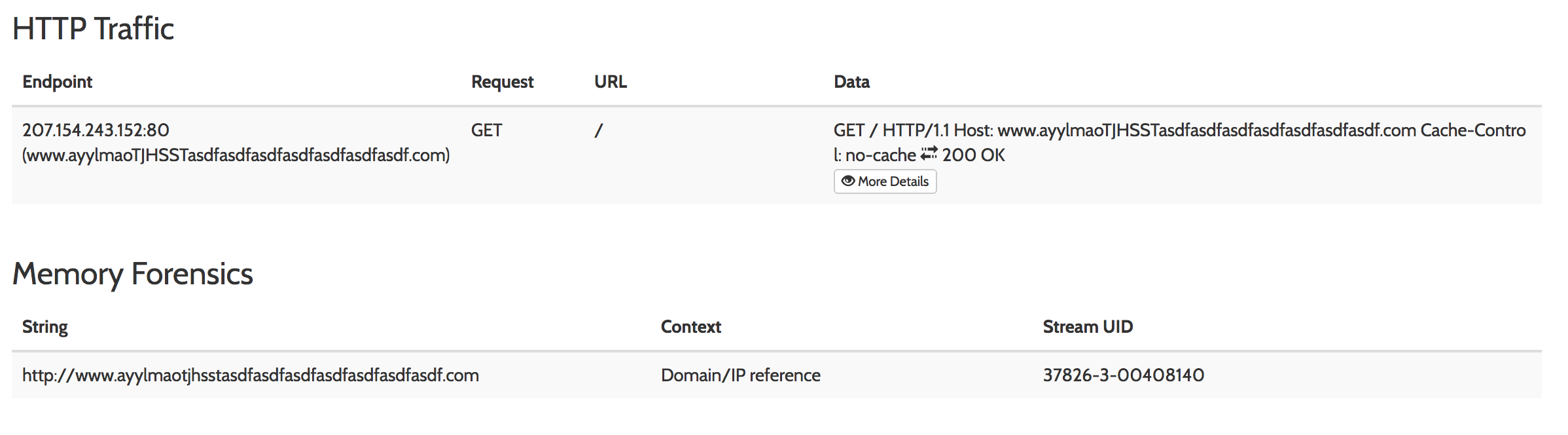
Shit! That domain really isn’t hiding itself, is it?
But wait! I hear you say, he never mentioned using dynamic analysis to look for a domain. Well okay then, let’s take a look at the sample itself and see if we can find it.
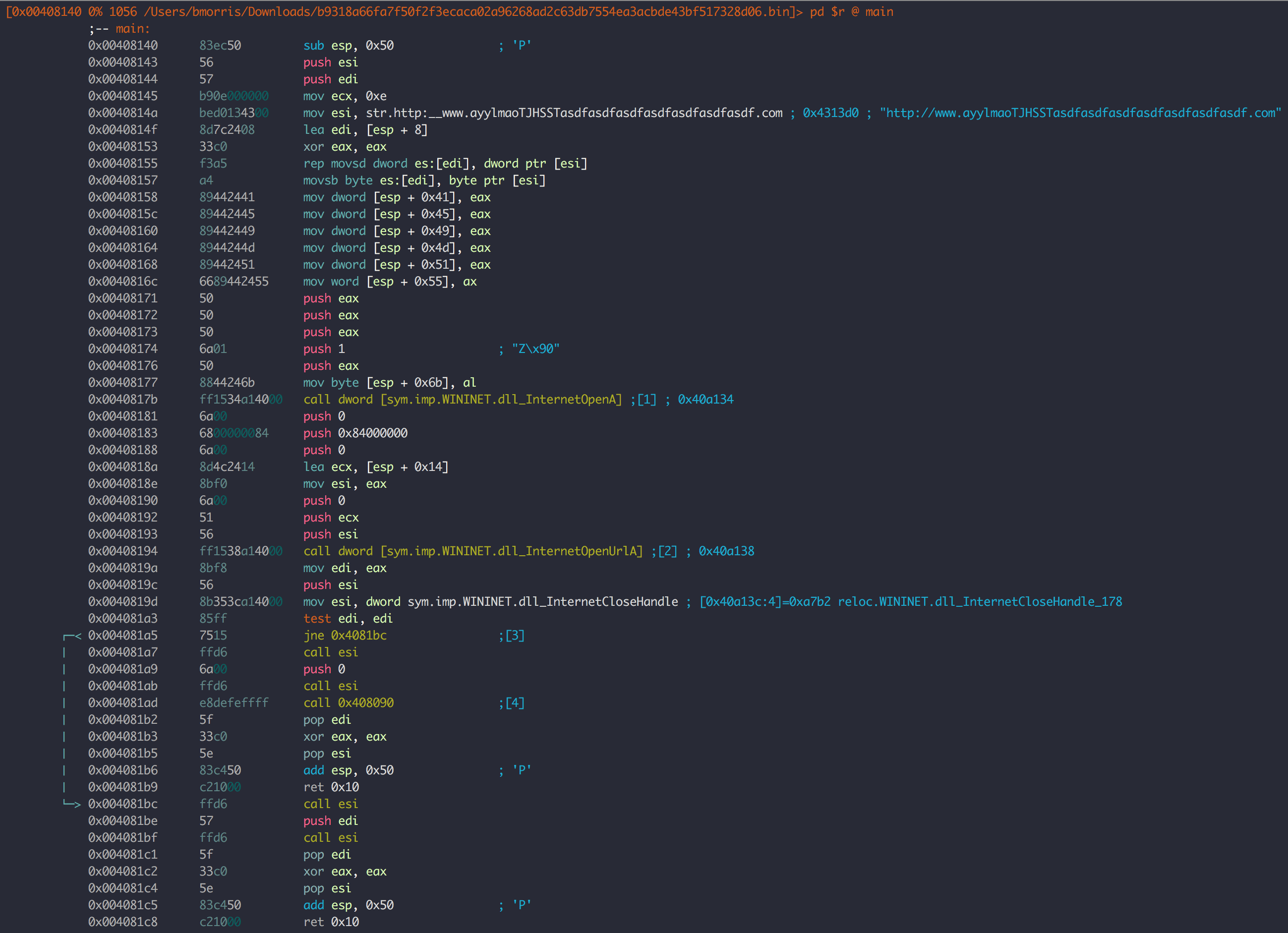
What you’re looking at is the disassembled code of the main (entrypoint) function in the WannaCry malware. Oh.. what’s that? That damn domain again!
Now, at this point MalwareTech would have dropped everything to check what the domain was doing, realized it wasn’t actually registered yet and jumped at the chance to register it before anyone else could, as it is a perfect way to track the spread of the Malware. This is where the “accidental” part comes in, it was later revealed that this domain was being used as a killswitch (or as a way to detect sandboxes which use inetsim, but we won’t get into that now).
But don’t take my word for it, why not read it in MalwareTech’s own words.
2017-10-12: Dr. Vesselin Bontchev informed me of an error in my article, I used a later sample of WannaCry, not the original one:
The original sample is this:https://t.co/poVyqLnpFz
— Vess (@VessOnSecurity) August 11, 2017
Kill switch begins with "iuqer...".
The sample I used was the sample who’s killswitch was registered by Matthieu Suiche (@msuiche). Although the killswitch is in the same exact place in both samples and just as easily discovered.