How I Reverse Malware
I told some guys on IRC that I would write a post about how I do my reverse engineering one day but have been pretty busy since then and wasn’t able to find the time to sit down and write it until now. Sorry it took so long.
This isn’t meant to be a step by step guide in setting this up, rather more of a rough guideline to get you started, chances are you aren’t using the same VM host as I am and everything will be different anyway.
Obviously if you’re running malware you will want to run it in a virtual environment, and I like the idea that if I accidentally run some shellcode during debugging that I haven’t read properly or misunderstood it won’t affect my real system. For this I use virtualbox. I chose virtualbox because it is free and has more features than VMWare’s free VMWare Player. Specifically I need the snapshot features for rolling back to known states easily when running malware in a lab environment.
I have multiple virtual Windows and Linux environments for running malware and they have all the tools I may need during testing (debuggers, disassemblers etc), even my developer workstation is a VM. Each VM runs inside a fully virtualized network, routing their traffic through virtualized pfsense routers. This way I can easily log and firewall traffic through pfsense when I need to monitor network access while running samples.
The main network contains two routers, the first of which is a Debian machine running dnsmasq and Tor. It is configured to hand out IP addresses in it’s network on eth1 and route all traffic that comes from eth1 through Tor. It also acts as a DNS server and resolves DNS queries through the Tor dns port. The second router inside this network is a pfsense 2.3.1 router that I use for a firewall and traffic logging. This pfsense router gets an upstream IP from the Tor router and hands out IP addresses to my analysis machines, meaning all traffic coming from the analysis machines is forced through my pfsense firewall first, then through Tor. This way malware cant figure out my home IP address even if it exploits a vulnerability in the pfsense control panel and I also don’t have lots of malicious traffic flowing straight from my house.
This is how traffic flows through my virtual network:
malware vm –> pfsense –> Tor router –> Tor network –> internet
Tor Router
First, let’s set up the Tor router. There are plenty of tutorials out there for doing this so I won’t get into it too much but these are the 4 steps you need to do:
- Install and configure bridge-utils
- Install and configure dnsmasq
- Install and configure Tor (with dnsport enabled)
- Configure the firewall to route traffic through Tor
There is a good tutorial for this on HowtoForge.
Once that is done we can configure the virtualbox network for this machine to have 2 adapters. Adapter 1 should just be simple and attached to the NAT. This will be eth0 on the machine. Adapter 2 should be in an internal network, you should have something similar to this:
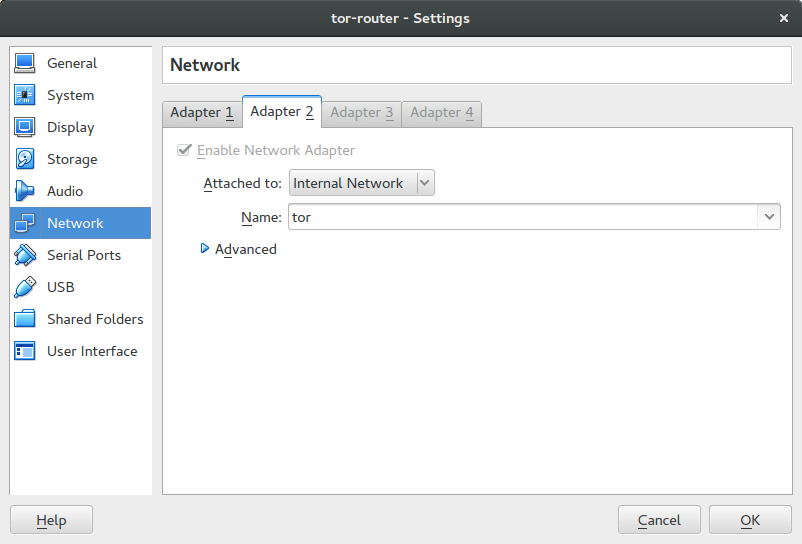
Pfsense Router
Create a new VM and configure the network to have 2 adapters like before. This time both will be internal adapters, the first one should be named the same as the internal adapter for the Tor router. This is where pfsense gets it’s network connectivity from. In the example before we named the network “tor” so we will name the network for adapter 1 on this VM the same. The next adapter can be called anything as long as it isn’t “tor”. I just called it “internal”.
Now we can install pfsense on the VM. Ensure that you select the correct adapters during setup, the upstream adapter should be eth0 and the adapter it hands out IP addresses on should be eth1.
Once this is done we can boot both the routers. I find that I get strange issues if I don’t boot the Tor router before the pfsense box.
VMs
Now we can create our reversing VMs. This step is completely up to you to decide what you need. The only thing that needs to be changed is the VMs should have only 1 network adapter and it should be an internal adapter with the network named the same as the adapter that pfsense is handing out IPs on. In our example we just called it “internal”. Once the VM is booted all traffic should be flowing through Tor, check your IP has changed before launching any malware.